200 search results - page 34 / 40 » A new approach on wearable game design and its evaluation |
SIGMOD
2008
ACM
15 years 6 months ago
2008
ACM
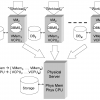
Virtual machine monitors are becoming popular tools for the deployment of database management systems and other enterprise software applications. In this paper, we consider a commo...
CVPR
2008
IEEE
14 years 2 months ago
2008
IEEE
Computer users with visual impairment cannot access the rich graphical contents in print or digital media unless relying on visual-to-tactile conversion, which is done primarily b...
IACR
2011
12 years 7 months ago
2011
Although anonymous authentication has been extensively studied, so far no scheme has been widely adopted in practice. A particular issue with fully anonymous authentication schemes...
RTSS
1997
IEEE
13 years 12 months ago
1997
IEEE
In [6], we proposed a new commit protocol, OPT, specially designed for use in distributed firm-deadline real-time database systems. OPT allows transactions to “optimistically�...
SIGMETRICS
2004
ACM
14 years 1 months ago
2004
ACM
This paper develops and evaluates new share-based scheduling algorithms for differentiated service quality in network services, such as network storage servers. This form of resou...