425 search results - page 66 / 85 » An approach to the evaluation of the performance of a discre... |
PLDI
2012
ACM
11 years 10 months ago
2012
ACM
When program verification tools fail to verify a program, either the program is buggy or the report is a false alarm. In this situation, the burden is on the user to manually cla...
ICCV
2009
IEEE
15 years 15 days ago
2009
IEEE
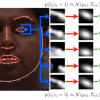
Local experts have been used to great effect for fitting deformable
models to images. Typically, the best location in
an image for the deformable model’s landmarks are found
t...
JMLR
2006
13 years 7 months ago
2006
Spam filtering poses a special problem in text categorization, of which the defining characteristic is that filters face an active adversary, which constantly attempts to evade fi...
CEC
2010
IEEE
13 years 5 months ago
2010
IEEE
This paper focuses on the application of a new ACO-based automatic programming algorithm to the classification task of data mining. This new model, called GBAP algorithm, is based ...
ICNP
2009
IEEE
14 years 2 months ago
2009
IEEE
—Wormhole attack is a severe threat to wireless ad hoc and sensor networks. Most existing countermeasures either require specialized hardware devices or make strong assumptions o...