162 search results - page 16 / 33 » Anonymity for continuous data publishing |
TMC
2008
13 years 5 months ago
2008
Continued advances in mobile networks and positioning technologies have created a strong market push for location-based applications. Examples include location-aware emergency resp...
KDD
2007
ACM
14 years 7 months ago
2007
ACM
Privacy-preserving data mining (PPDM) is an important topic to both industry and academia. In general there are two approaches to tackling PPDM, one is statistics-based and the oth...
COLCOM
2007
IEEE
14 years 1 months ago
2007
IEEE
—In many applications, transaction data arrive in the form of high speed data streams. These data contain a lot of information about customers that needs to be carefully managed ...
SIGMOD
2010
ACM
14 years 4 days ago
2010
ACM
Serious concerns on privacy protection in social networks have been raised in recent years; however, research in this area is still in its infancy. The problem is challenging due ...
ICDE
2009
IEEE
15 years 7 months ago
2009
IEEE
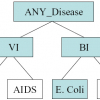
Existing approaches on privacy-preserving data publishing rely on the assumption that data can be divided into quasi-identifier attributes (QI) and sensitive attribute (SA). This ...