197 search results - page 19 / 40 » Assessing Databases in .NET - Comparing Approaches |
120
click to vote
ACMSE
2005
ACM
15 years 7 months ago
2005
ACM
Accurate identification of misuse is a key factor in determining appropriate ways to protect systems. Modern intrusion detection systems often use alerts from different sources su...
108
Voted
CVPR
2000
IEEE
16 years 4 months ago
2000
IEEE
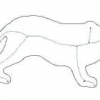
There has recently been significant interest in using repions based on abstractions of Blum's skeleton into a graph, for qualitative shape matching. The application of these ...
97
Voted
SIGMETRICS
2010
ACM
15 years 17 days ago
2010
ACM
Data center availability is critical considering the explosive growth in Internet services and people’s dependence on them. Furthermore, in recent years, sustainability has beco...
151
click to vote
SIGMOD
2012
ACM
13 years 4 months ago
2012
ACM
As cloud computing environments become explosively popular, dealing with unpredictable changes, uncertainties, and disturbances in both systems and environments turns out to be on...
215
Voted
PODS
2009
ACM
16 years 2 months ago
2009
ACM
As advances in technology allow for the collection, storage, and analysis of vast amounts of data, the task of screening and assessing the significance of discovered patterns is b...