443 search results - page 62 / 89 » Compensation-Aware Runtime Monitoring |
221
Voted
SIGMOD
2008
ACM
17 years 1 months ago
2008
ACM
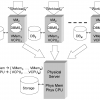
Virtual machine monitors are becoming popular tools for the deployment of database management systems and other enterprise software applications. In this paper, we consider a commo...
119
Voted
DAC
2005
ACM
16 years 3 months ago
2005
ACM
In the design of highly complex, heterogeneous, and concurrent systems, deadlock detection and resolution remains an important issue. In this paper, we systematically analyze the ...
117
click to vote
WWW
2004
ACM
16 years 3 months ago
2004
ACM
ReAgents are remotely executing agents that customize Web browsing for non-standard resource-limited clients. A reAgent is essentially a "one-shot" mobile agent that act...
148
click to vote
ESORICS
2002
Springer
16 years 2 months ago
2002
Springer
Resource security pertains to the prevention of unauthorized usage of system resources that may not directly cause corruption or leakage of information. A common breach of resource...
113
Voted
ACHI
2009
IEEE
15 years 9 months ago
2009
IEEE
In today’s continuously changing markets newly developed products often do not meet the demands and expectations of customers. Research on this problem identified a large gap b...