350 search results - page 64 / 70 » Complexity of Planning with Partial Observability |
CTRSA
2008
Springer
13 years 9 months ago
2008
Springer
Abstract. Camellia and MISTY1 are Feistel block ciphers. In this paper, we observe that, when conducting impossible differential cryptanalysis on Camellia and MISTY1, their round s...
MOBICOM
2010
ACM
13 years 8 months ago
2010
ACM
Mobility traces of people and vehicles have been collected and published to assist the design and evaluation of mobile networks, such as large-scale urban sensing networks. Althou...
PR
2006
13 years 7 months ago
2006
By analyzing the similarities between bit streams coming from a network of motion detectors, we can recover the network geometry and discover structure in the human behavior being...
120
click to vote
Publication
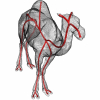
In this paper, we present a novel framework for computing centerlines for both 2D and 3D shape analysis. The framework works as follows: an object centerline point is
selected aut...
115
click to vote
Presentation
In this paper, we present a novel framework for computing centerlines for both 2D and 3D shape analysis. The framework works as follows: an object centerline point is selected auto...