832 search results - page 68 / 167 » Effect of Malicious Synchronization |
DEXA
2000
Springer
14 years 2 months ago
2000
Springer
The event calculus is a logic programming formalism for representing events and their effects especially in database applications. This paper presents the use of the event calculus...
KDD
2005
ACM
14 years 10 months ago
2005
ACM
One fundamental task in near-neighbor search as well as other similarity matching efforts is to find a distance function that can efficiently quantify the similarity between two o...
CHI
2003
ACM
14 years 10 months ago
2003
ACM
A tension exists between designers' comfort with physical artifacts and the need for effective remote collaboration: physical objects live in one place. Previous research and...
ICIP
2005
IEEE
14 years 11 months ago
2005
IEEE
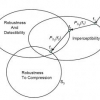
We introduce a set theoretic framework for watermarking and illustrate its effectiveness by designing a hierarchical semi-fragile watermark that is tolerant to compression and all...
ICDE
2008
IEEE
14 years 11 months ago
2008
IEEE
Abstract-- Privacy preservation in data mining demands protecting both input and output privacy. The former refers to sanitizing the raw data itself before performing mining. The l...