1380 search results - page 235 / 276 » Learning Hierarchical Shape Models from Examples |
148
click to vote
SCN
2010
Springer
15 years 26 days ago
2010
Springer
Exposure of a secret key is a significant threat in practice. As a notion of security against key exposure, Dodis et al. advocated key-insulated security, and proposed concrete k...
115
Voted
UAI
2003
15 years 3 months ago
2003
We formulate a principle for classification with the knowledge of the marginal distribution over the data points (unlabeled data). The principle is cast in terms of Tikhonov styl...
320
Voted
Tutorial
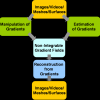
The last decade has seen a tremendous interest in gradient domain manipulation techniques for applications in vision and graphics including retinex, high dynamic range (HDR) tone m...
112
click to vote
CODES
2006
IEEE
15 years 8 months ago
2006
IEEE
Middleware for parallel and distributed systems is designed to virtualize computation and communication resources so that a more and consistent view of those resources is presente...
CVPR
2006
IEEE
15 years 8 months ago
2006
IEEE
A wide range of methods have been proposed to detect and recognize objects. However, effective and efficient multiviewpoint detection of objects is still in its infancy, since mo...