1833 search results - page 14 / 367 » Mechanized Verification with Sharing |
112
click to vote
Lecture Notes
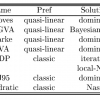
Survey Chapters on Mechanism Design and Electronic Markets, Shared by David Parkes
131
click to vote
FMCAD
2008
Springer
15 years 2 months ago
2008
Springer
We present a method for verifying information flow properties of software programs using inductive assertions and theorem proving. Given a program annotated with information flow a...
CCS
2008
ACM
15 years 2 months ago
2008
ACM
Usage control is a generalization of access control that also addresses how data is used after it is released. We present a formal model for different mechanisms that can enforce ...
103
click to vote
APSCC
2006
IEEE
15 years 2 months ago
2006
IEEE
Detecting intrusions at host level is vital to protecting shared resources in grid, but traditional Host-based Intrusion Detecting System (HIDS) is not suitable for grid environme...
118
click to vote
ICISC
2004
15 years 2 months ago
2004
An identity (ID)-based signature scheme allows any pair of users to verify each other's signatures without exchanging public key certificates. With the advent of Bilinear maps...