125 search results - page 18 / 25 » Non-Exposure Location Anonymity |
PERCOM
2005
ACM
14 years 9 months ago
2005
ACM
Pervasive computing is a future technology that provides a user with the capability to compute and communicate from everywhere. In a pervasive computing environment, a user interac...
CSE
2009
IEEE
14 years 4 months ago
2009
IEEE
—Modern consumer wireless devices are increasingly powerful, making them attractive to use as wireless sensor nodes. At the same time, many use protocol suites such as Bluetooth ...
PERVASIVE
2005
Springer
14 years 3 months ago
2005
Springer
Abstract. In this paper we introduce the simultaneous tracking and activity recognition (STAR) problem, which exploits the synergy between location and activity to provide the info...
ESORICS
2009
Springer
14 years 4 months ago
2009
Springer
The increasing availability of space-time trajectories left by location-aware devices is expected to enable novel classes of applications where the discovery of consumable, concise...
Publication
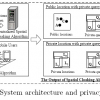
Existing location-based services provide specialized services to their customers based on the knowledge of their exact locations. With untrustworthy servers, location-based service...