632 search results - page 84 / 127 » Two Facets of Authentication |
SIGMOD
2011
ACM
12 years 11 months ago
2011
ACM
Debugging a database engine is an arduous task due to the complexity of the query workloads and systems. The first step in isolating a bug involves identifying a sequence of step...
ICCV
2009
IEEE
15 years 1 months ago
2009
IEEE
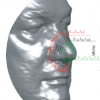
In this paper we explore the use of shapes of noses for
performing partial human biometrics. The basic idea is to
represent nasal surfaces using indexed collections of isocurves,...
ICIP
2000
IEEE
14 years 10 months ago
2000
IEEE
Media hashing is an alternative to achieve many applications previously accomplished with watermarking. The major disadvantage of the existing media hashing technologies is their ...
ICPR
2008
IEEE
14 years 10 months ago
2008
IEEE
Cancelable biometric systems are gaining in popularity for use in person authentication for applications where the privacy and security of biometric templates are important consid...
INFOCOM
2009
IEEE
14 years 3 months ago
2009
IEEE
—Given that wireless communication occurs in a shared and inherently broadcast medium, the transmissions are vulnerable to undesired eavesdropping. This occurs even when a point-...