43 search results - page 6 / 9 » What Enterprise Architecture and Enterprise Systems Usage Ca... |
EDBT
2011
ACM
12 years 11 months ago
2011
ACM
Data integration systems offer users a uniform interface to a set of data sources. Previous work has typically assumed that the data sources are independent of each other; however...
HOTOS
2003
IEEE
14 years 23 days ago
2003
IEEE
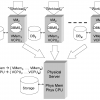
Cerium is a trusted computing architecture that protects a program’s execution from being tampered while the program is running. Cerium uses a physically tamperresistant CPU and...
SIGMOD
2008
ACM
15 years 6 months ago
2008
ACM
Virtual machine monitors are becoming popular tools for the deployment of database management systems and other enterprise software applications. In this paper, we consider a commo...
DGO
2003
13 years 8 months ago
2003
The Internet has recently become the medium of interaction with large volumes of data. Enterprises in the public and private sectors made their databases available over the Intern...
SEMWEB
2004
Springer
14 years 25 days ago
2004
Springer
The Semantic Web is bound to be untrustworthy and inconsistent. In this paper, we present an initial approach for obtaining useful information in such an environment. In particular...