119
click to vote
ICIP
2006
IEEE
16 years 3 months ago
2006
IEEE
In this paper, we propose to combine formally noise and shape priors in region-based active contours. On the one hand, we use the general framework of exponential family as a prio...
107
Voted
ICIP
2006
IEEE
16 years 3 months ago
2006
IEEE
Stream authentication methods usually impose overhead and dependency among packets. The straightforward application of state-of-the-art rate-distortion (R-D) optimized streaming t...
122
click to vote
ICIP
2006
IEEE
16 years 3 months ago
2006
IEEE
For the non-local denoising approach presented by Buades et al., remarkable denoising results are obtained at high expense of computational cost. In this paper, a new algorithm th...
ICIP
2006
IEEE
16 years 3 months ago
2006
IEEE
111
click to vote
ICIP
2006
IEEE
16 years 3 months ago
2006
IEEE
Abstract-- This paper presents an authentication watermarking method which can localize the tampering regions in fine granularity. Unlike the previous block-wise Tampering-Localiza...
ICIP
2006
IEEE
16 years 3 months ago
2006
IEEE
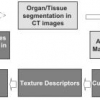
The research presented in this article is aimed at the development of an automated imaging system for classification of tissues in medical images obtained from Computed Tomography...
111
click to vote
ICIP
2006
IEEE
16 years 3 months ago
2006
IEEE
A novel statistical approch for detection and tracking of objects is presented here, which uses both edge and color information in a particle filter. The approach does not need an...
121
click to vote
ICIP
2006
IEEE
16 years 3 months ago
2006
IEEE
In order to summarize a video consisting of a sequence of different activities, there are three fundamental problems: tracking the objects of interest, detecting the activity chan...
110
click to vote
ICIP
2006
IEEE
16 years 3 months ago
2006
IEEE
Meetings are an integral part of business life for any organization. In previous work, we have developed a physical awareness system called CAMEO (Camera Assisted Meeting Event Ob...
114
click to vote
ICIP
2006
IEEE
16 years 3 months ago
2006
IEEE
In this paper we propose a method for video delivery over bit error channels. In particular, we propose a rate distortion optimal method for slicing and unequal error protection (...