519 search results - page 99 / 104 » Control flow obfuscation with information flow tracking |
LCN
1998
IEEE
14 years 29 days ago
1998
IEEE
Abstract-- The emergence of nomadic applications have recently generated much interest in wireless network infrastructures that support real-time communications. In this paper, we ...
132
click to vote
Publication
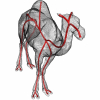
In this paper, we present a novel framework for computing centerlines for both 2D and 3D shape analysis. The framework works as follows: an object centerline point is
selected aut...
126
click to vote
Presentation
In this paper, we present a novel framework for computing centerlines for both 2D and 3D shape analysis. The framework works as follows: an object centerline point is selected auto...
HPCA
2008
IEEE
14 years 9 months ago
2008
IEEE
Dynamic binary translation (DBT) is a runtime instrumentation technique commonly used to support profiling, optimization, secure execution, and bug detection tools for application...
RE
2010
Springer
13 years 3 months ago
2010
Springer
Today, companies are required to be in control of their IT assets, and to provide proof of this in the form of independent IT audit reports. However, many companies have outsourced...