985 search results - page 128 / 197 » On the validity of digital signatures |
DAC
1999
ACM
14 years 11 months ago
1999
ACM
Recently, a number of watermarking-based intellectual property protection techniques have been proposed. Although they have been applied to different stages in the design process ...
ISBI
2006
IEEE
14 years 10 months ago
2006
IEEE
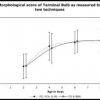
We are studying the genetic influence on rates of age related muscle degeneration in C. elegans. For this, we built pattern recognition tools to calculate a morphological score gi...
PERCOM
2004
ACM
14 years 9 months ago
2004
ACM
Sleep deprivation attacks are a form of denial of service attack whereby an attacker renders a pervasive computing device inoperable by draining the battery more quickly than it w...
ISBI
2009
IEEE
14 years 4 months ago
2009
IEEE
Biological images have the potential to reveal complex signatures that may not be amenable to morphological modeling in terms of shape, location, texture, and color. An effective ...
SERA
2009
Springer
14 years 4 months ago
2009
Springer
In the context of computer programming, the importance of computer assistance is being understood by many developer communities. Developers are e.g. using the same well known expre...