567 search results - page 61 / 114 » Reconstructing Numbers from Pairwise Function Values |
100
click to vote
FC
2007
Springer
15 years 8 months ago
2007
Springer
Responding to the PIN cracking attacks from Berkman and Ostrovsky (FC 2007), we outline a simple solution called salted-PIN. A randomly generated salt value of adequate length (e.g...
130
click to vote
BMCBI
2010
15 years 2 months ago
2010
Background: Coevolutionary systems like hosts and their parasites are commonly used model systems for evolutionary studies. Inferring the coevolutionary history based on given phy...
123
click to vote
IPPS
2000
IEEE
15 years 6 months ago
2000
IEEE
Many techniques for increasing the amount of instruction-level parallelism (ILP) put increased pressure on the registers inside a CPU. These techniques allow for more operations t...
133
click to vote
ICCV
2009
IEEE
16 years 7 months ago
2009
IEEE
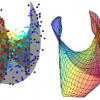
We present a manifold learning approach to dimensionality
reduction that explicitly models the manifold as a mapping
from low to high dimensional space. The manifold is
represen...
119
click to vote
ICPR
2008
IEEE
16 years 3 months ago
2008
IEEE
Fuzzy vault has been shown to be an effective technique for securing fingerprint minutiae templates. Its security depends on the difficulty in identifying the set of genuine minut...