491 search results - page 94 / 99 » An Efficient Distributed PKI for Structured P2P Networks |
CORR
2008
Springer
13 years 7 months ago
2008
Springer
The Trinity [1] spam classification system is based on a distributed hash table that is implemented using a structured peer-to-peer overlay. Such an overlay must be capable of proc...
IPPS
2010
IEEE
13 years 5 months ago
2010
IEEE
Quantum chemistry applications such as the General Atomic and Molecular Electronic Structure System (GAMESS) that can execute on a complex peta-scale parallel computing environment...
CCS
2008
ACM
13 years 9 months ago
2008
ACM
Hash tables are fundamental data structures that optimally answer membership queries. Suppose a client stores n elements in a hash table that is outsourced at a remote server so t...
VLSID
2006
IEEE
14 years 7 months ago
2006
IEEE
With device size shrinking and fast rising frequency ranges, effect of cosmic radiations and alpha particles known as Single-Event-Upset (SEU), Single-Eventtransients (SET), is a ...
CVPR
2009
IEEE
15 years 2 months ago
2009
IEEE
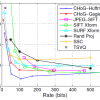
Establishing visual correspondences is an essential component
of many computer vision problems, and is often done
with robust, local feature-descriptors. Transmission and
storag...